Cyrus
Field IDS
In industrial control systems, usually between PLCs and control equipment in the field, there is no monitoring and control beyond the information in the PLC. In this case, if the PLC is infected with malware, it can cause widespread destruction by sending and displaying false information to the HMI and simultaneously sending destructive commands to the equipment in the field. In fact, the operator does not have any other tools for validation except the information available in the HMI.
The Stuxnet virus used exactly this weakness and by infecting PLCs while displaying false information to the operators, it sent destructive commands to the centrifuges at the same time and has caused disruption in the control system. The Cyrus Field IDS product is an industrial IDS in the field area, which by sniffing the commands issued to the equipment in the field area, shows the status of the commands received by the equipment directly to the operator. The operator can match the commands actually received by the field with the information sent by the PLC to the HMI.
If there is a difference between the information received from the PLC and Cyrus Filed IDS, the industrial network is definitely infected with Malware. If a product like Cyrus Field IDS was installed on the line at the time of the Stuxnet attack This anomaly was immediately detectable. If both Cyrus Field IDS and Cyrus Firewall products are used in an industrial network, this analysis can be done by Firewall. In this case, the Firewall can intelligently detect this abnormality and inform the operator of abnormal conditions on the line by sending an Alert. Due to the use of different hardware, different companies have developed their software protocols according to the conditions, many of which are based on RS232 or RS485 serial port.
In addition to being able to detect attacks and intrusions at the TCP/IP level, industrial IDSs must also be able to detect attacks in the most industrial ZONE End Point. In the following, we explain in more technical detail how the Cyrus Field IDS product can detect attacks like Stuxnet: In 1987 and 1988, the Stuxnet malware infected the control system of the Natanz nuclear facility and caused disruption in the uranium enrichment process.
Simply put: what Stuxnet did was that after penetrating the system, if Step7 software (which is used to program Siemens PLCs) is installed) implemented a wrapper on its Dll files so that when downloading the program written in the PLC, it would first add its destructive dll block and then place the original program. All these works were done legally and were done by the main dll and the communication protocol of Siemens, with the difference that it added a Stuxnet block interface between the program and the main dll. This block was responsible for controlling the drive of the centrifuge motor and stirring the production cycle.
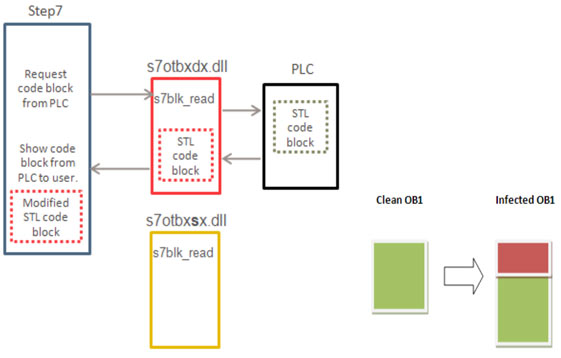
Siemens uses several software protocols and hardware media to control and monitor its equipment, including:
- S7comm over TCP/IP
- S7commPlus over TCP/IP
- Profibus over RS485
- Profinet over Network L2 Layer
Cited. Due to the history of Siemens and the wide range of its products, these protocols have been designed and developed by Siemens itself and have been standardized. Now let's go back to the Stuxnet scenario.
According to the reports presented, the uranium enrichment cycle and the operation of the centrifuges were as follows:
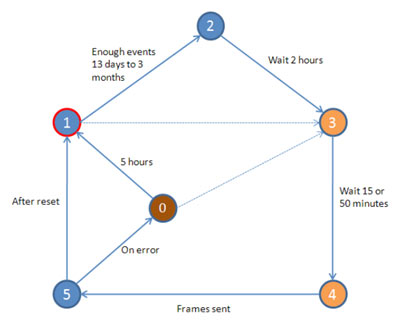
The normal path of execution is 1-2-3-4-5-1 – as shown by the solid, blue arrows in the diagram
in all these stages, the centrifuges must have different engine revolutions, which are detailed in the reports of Symantec and Kaspersky and you can read them.
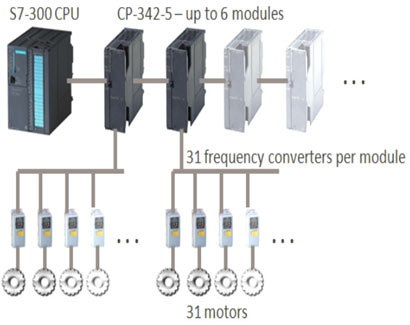
According to the documents published in the nuclear facilities, two motor inverters from two companies have been used, which are KFC750V3 of Ferraro Paya Tehran and Vacon NX, respectively. The important point in this matter is Stuxnet's intrusion and changing the engine speed and disrupting the uranium enrichment cycle.The communication between PLC and motor drives was by Profibus protocol and RS485 media. According to the topics presented, if we put several layers of industrial firewall on the TCP/IP platform, we still cannot stop the worms that act like Stuxnet. Because PLC programming was done legally and logically and normally through Siemens protocol. In the industry, because programmers mostly use personal computers with low security to program PLC, penetration is almost inevitable and the only solution is prevention, risk reduction and penetration detection at the end point of the production line.
If an intrusion detection system (Industrial IDS) was installed on Profibus lines in nuclear facilities, it would be easy to determine when and how to change the spin of the centrifuges, and any intrusion could be detected.
Also, with this method, it is possible to debug the line in a way, and it is easy to distinguish between intrusion and error. Cyrus Field IDS product complements Cyrus industrial firewall.
Cyrus industrial firewall has IPS/IDS capabilities on TCP platform. But in order to discover malware with the same functionality as Stuxnet, we also need to monitor the control equipment in the field in terms of security. Cyrus Field IDS product is a device that easily detects conventional protocols on RS485 and serial lines and detects intrusions and attacks on this platform.
The protocols that the CYRUS device can recognize on the serial and RS485 platform are:
- Profibas
- IEC 101 / 102
- DNP3 Serial
- Modbus RTU
System architecture:
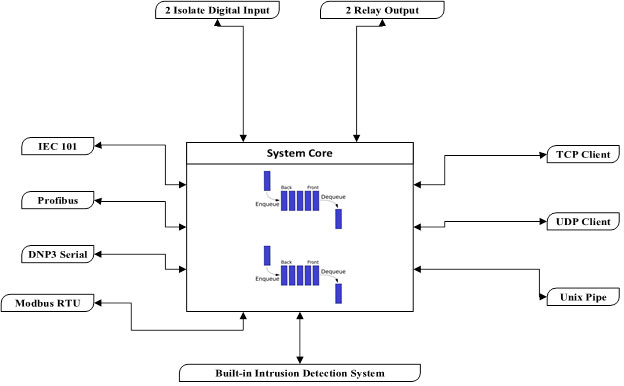
Or paying attention to the system architecture, this device is designed in such a way that it can provide the following capabilities:
- Work as standalone as IDS or as a supplement with Cyrus firewall
- Receive, validate and verify multiple protocols at the same time according to the number of serial ports available in hardware
- Send error reports in case of incomplete or Malform frames
- Simultaneous sending of received packets to several servers in one direction
- Sending packets with TCP, UDP protocols
- Sending received packets through Linux Pipe
- Checking the signal level through the oscilloscope built on the device and detecting the rs485 bus signaling error
- Very suitable for troubleshooting serial lines and the mentioned protocols

